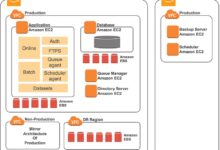
Identity Management AWS: 7 Ultimate Power Strategies
In the digital labyrinth of cloud computing, where data flows like rivers and access is the currency, one truth stands firm: identity is the new perimeter. Identity Management AWS isn’t just a tool—it’s the scientific backbone of secure, scalable, and intelligent cloud ecosystems.
Understanding Identity Management AWS: The Foundation of Cloud Security

At the heart of Amazon Web Services (AWS) lies a powerful, flexible, and deeply integrated system for managing digital identities. Identity Management AWS refers to the suite of tools, policies, and protocols that govern who—or what—can access resources within an AWS environment. It’s not merely about usernames and passwords; it’s about establishing trust in a distributed, dynamic world where servers are ephemeral and workloads span continents.
What Is Identity Management AWS?
Identity Management AWS is primarily powered by AWS Identity and Access Management (IAM), a service that enables administrators to manage access to AWS services and resources securely. IAM allows you to create and manage AWS users and groups, assign permissions using policies, and enforce security best practices such as multi-factor authentication (MFA) and least privilege access.
- IAM enables granular control over AWS resource access.
- It supports both human users and machine identities (like EC2 instances).
- It integrates with other AWS services such as S3, EC2, Lambda, and CloudTrail.
According to AWS’s official documentation, IAM is the cornerstone of AWS security, providing the foundational layer upon which all access decisions are made.
The Evolution of Identity in the Cloud Era
Traditional identity models were built around static networks and on-premises infrastructure. In contrast, cloud environments demand a zero-trust approach, where every request must be authenticated and authorized regardless of origin. Identity Management AWS has evolved to meet this challenge by embracing principles of decentralization, automation, and policy-as-code.
Modern identity management in AWS now includes federated identities via SAML 2.0, integration with external identity providers like Microsoft Active Directory through AWS Directory Service, and support for OAuth 2.0 and OpenID Connect. This evolution reflects a broader industry shift toward identity-centric security models.
“In the cloud, there is no castle wall. Identity becomes the moat and the drawbridge.” — AWS Security Best Practices Guide
Core Components of Identity Management AWS
To master Identity Management AWS, one must understand its core building blocks. These components work together to create a robust, auditable, and scalable access control framework.
AWS Identity and Access Management (IAM)
IAM is the central nervous system of Identity Management AWS. It allows organizations to define roles, users, groups, and policies that dictate access rights. Every action taken within AWS—whether launching an EC2 instance or reading from an S3 bucket—must be authorized by IAM.
- Users represent individual people or applications requiring AWS access.
- Groups are collections of users that simplify permission management.
- Roles are temporary credentials assigned to entities (users, services, or federated identities) that define what they can do.
For example, a developer might belong to a ‘Developers’ group with read-only access to production databases but full access to development environments. Roles are especially critical for cross-account access and granting permissions to AWS services themselves, such as allowing an EC2 instance to read from S3.
Policy Types and Structure in IAM
Policies are JSON documents that explicitly define permissions. There are two main types: managed policies and inline policies. Managed policies can be attached to multiple users, groups, or roles and are easier to maintain at scale.
A typical policy includes:
- Version: Specifies the language version (e.g., 2012-10-17).
- Statement: An array of individual permission statements.
- Effect: Either ‘Allow’ or ‘Deny’.
- Action: The specific API actions permitted (e.g., s3:GetObject).
- Resource: The ARN (Amazon Resource Name) of the resource being accessed.
- Condition: Optional constraints based on time, IP address, or MFA status.
An example of a policy allowing S3 read access:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::example-bucket/*"
}
]
}
This structure ensures precision and repeatability in access control, enabling automation and compliance auditing.
Multi-Factor Authentication (MFA) and Security Tokens
One of the most effective ways to strengthen Identity Management AWS is by enforcing MFA. MFA requires users to present two or more forms of identification: something they know (password), something they have (a hardware or virtual MFA device), and optionally something they are (biometrics).
AWS supports virtual MFA apps (like Google Authenticator), U2F security keys, and hardware MFA devices. When enabled, MFA significantly reduces the risk of unauthorized access even if credentials are compromised.
Additionally, AWS uses temporary security tokens through services like AWS Security Token Service (STS). These tokens are issued when assuming roles and have a limited lifespan, reducing the exposure window for credential misuse.
“Never underestimate the value of time-bound credentials in minimizing blast radius during breaches.” — AWS Well-Architected Framework
Identity Federation and Single Sign-On with Identity Management AWS
As enterprises grow and integrate with third-party systems, managing identities across multiple domains becomes complex. Identity Management AWS addresses this through federation and Single Sign-On (SSO), enabling seamless and secure access without duplicating user accounts.
What Is Identity Federation?
Identity federation allows users from external identity providers (IdPs) to access AWS resources without creating separate IAM users. This is achieved using standards like SAML 2.0 or OpenID Connect (OIDC). For instance, employees using corporate Active Directory can log in to AWS via their existing credentials.
- Federation eliminates the need to manage separate AWS user accounts for large organizations.
- It centralizes identity management, improving compliance and reducing administrative overhead.
- It enables just-in-time role assumption, where users are granted temporary access based on their identity attributes.
Organizations often use AWS identity federation to integrate with Microsoft ADFS, Okta, or Azure AD, allowing secure cross-cloud access.
Implementing SSO with AWS SSO
AWS Single Sign-On (SSO) is a fully managed service that enables users to log in to the AWS Management Console or AWS CLI using their corporate credentials. AWS SSO integrates with AWS Organizations to centrally manage access across multiple AWS accounts.
Key benefits include:
- Centralized user access management across AWS accounts.
- Integration with SCIM (System for Cross-domain Identity Management) for automated user provisioning.
- Support for assigning permission sets (collections of policies) to users or groups.
For example, a finance team can be granted read-only billing access across all accounts, while a DevOps team receives administrator access only to specific environments. This granular control enhances both security and operational efficiency.
Federated Access Scenarios and Best Practices
Federated access is particularly useful in hybrid environments, mergers and acquisitions, and partner ecosystems. Best practices include:
- Always map federated users to IAM roles, not IAM users.
- Use attribute-based role mapping to dynamically assign roles based on group membership or job function.
- Enforce MFA at the IdP level before allowing role assumption.
A common scenario involves a company using Okta as its IdP. When a user attempts to access AWS, Okta authenticates them and sends a SAML assertion to AWS, which then grants temporary credentials based on a pre-configured role. This process is transparent to the end-user and highly secure.
Role-Based Access Control (RBAC) and Policy Design in Identity Management AWS
Effective access control in AWS hinges on well-designed policies and a clear understanding of Role-Based Access Control (RBAC). RBAC ensures that users and systems have only the permissions necessary to perform their functions—no more, no less.
Principles of Least Privilege and Separation of Duties
The principle of least privilege is a cornerstone of Identity Management AWS. It dictates that every entity should have the minimum level of access required to perform its job. This reduces the attack surface and limits the damage from compromised accounts.
Separation of duties complements this by ensuring that no single user has end-to-end control over critical operations. For example, one team might deploy code, while another manages production databases.
- Use IAM policy simulators to test permissions before deployment.
- Avoid using full administrative privileges for daily tasks.
- Regularly audit and remove unused policies and roles.
AWS provides tools like IAM Access Analyzer and IAM Policy Validator to help enforce these principles.
Creating Custom Policies vs. Using Managed Policies
While AWS offers a wide range of AWS-managed policies (e.g., AmazonS3ReadOnlyAccess), organizations often need custom policies to meet specific compliance or operational requirements.
Custom policies offer greater flexibility but require careful design to avoid over-permissioning. Best practices include:
- Start with AWS managed policies and extend them as needed.
- Use condition keys to restrict access by time, IP, or MFA status.
- Document all custom policies and review them during security audits.
For instance, a policy might allow EC2 start/stop actions only during business hours:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:StartInstances",
"ec2:StopInstances"
],
"Resource": "*",
"Condition": {
"NumericLessThan": {
"aws:CurrentTime": "18000"
},
"NumericGreaterThan": {
"aws:CurrentTime": "06000"
}
}
}
]
}
Permission Boundaries and Service Control Policies
Advanced Identity Management AWS configurations use permission boundaries and Service Control Policies (SCPs) to enforce organizational governance.
Permission boundaries are advanced IAM features that set the maximum permissions a user or role can have. They are useful in delegating administrative tasks without granting full admin rights.
SCPs, part of AWS Organizations, allow administrators to set guardrails across multiple AWS accounts. For example, an SCP can prevent any account in the organization from deleting S3 buckets or launching EC2 instances in certain regions.
- SCPs are not standalone permissions—they only restrict existing permissions.
- They are applied at the organization unit (OU) level.
- They help meet compliance requirements like GDPR, HIPAA, or SOC 2.
Together, these tools enable large enterprises to maintain centralized control while allowing decentralized innovation.
Advanced Identity Management AWS: Integrating with External Systems
Modern enterprises rarely operate in isolation. Identity Management AWS must interoperate with external directories, cloud applications, and DevOps pipelines. This section explores how AWS integrates with broader IT ecosystems.
Integrating AWS with Active Directory
Many organizations rely on Microsoft Active Directory (AD) for user management. AWS supports integration through AWS Directory Service, which offers several options:
- AWS Managed Microsoft AD: A fully managed Active Directory in the cloud.
- AD Connector: A proxy that connects on-premises AD to AWS without syncing credentials.
- AD Trust Relationships: Enables cross-directory resource access.
This integration allows users to log in to AWS using their corporate AD credentials and enables group-based access control. For example, members of the ‘Finance’ AD group can be automatically mapped to an IAM role with billing access.
Learn more at AWS Directory Service documentation.
Using OAuth 2.0 and OpenID Connect
For web and mobile applications, Identity Management AWS supports OAuth 2.0 and OpenID Connect (OIDC) through Amazon Cognito. Cognito allows developers to add user sign-up, sign-in, and access control to apps quickly.
With OIDC, third-party identity providers like Google, Facebook, or Apple can authenticate users, and AWS assumes roles based on those identities. This is ideal for customer-facing applications where managing millions of user accounts directly would be impractical.
- Cognito User Pools handle authentication.
- Identity Pools provide temporary AWS credentials for federated users.
- Supports social login, SAML, and custom authentication flows.
This model scales effortlessly and reduces the burden on internal IT teams.
Automating Identity Management with Infrastructure as Code
In DevOps environments, Identity Management AWS must be version-controlled and repeatable. Tools like AWS CloudFormation, Terraform, and AWS CDK allow teams to define IAM roles, policies, and users as code.
Benefits include:
- Consistent deployment across environments (dev, test, prod).
- Change tracking and rollback capabilities.
- Integration with CI/CD pipelines for automated testing and deployment.
For example, a Terraform script can define an IAM role for a Lambda function, attach a policy allowing S3 read access, and deploy it as part of a larger application stack—all without manual intervention.
“Infrastructure as code transforms identity management from a manual chore into a scalable, auditable process.” — DevOps Research and Assessment (DORA)
Security Monitoring and Auditing in Identity Management AWS
No identity system is complete without robust monitoring and auditing. Identity Management AWS provides powerful tools to detect anomalies, investigate incidents, and prove compliance.
Using AWS CloudTrail for Audit Logging
AWS CloudTrail is the primary tool for tracking user activity and API usage across AWS accounts. It records every action taken by IAM users, roles, and services, including who made the request, what service was accessed, and from which IP address.
- CloudTrail logs can be stored in S3 and analyzed with Amazon Athena or AWS Lake Formation.
- It supports event history and trail creation for continuous logging.
- Integration with Amazon EventBridge enables real-time alerts on suspicious activities.
For example, a CloudTrail alert can trigger if a root account is used to launch an EC2 instance—a high-risk event that should be investigated immediately.
Implementing IAM Access Analyzer
IAM Access Analyzer helps identify unintended resource exposures by analyzing policies for cross-account access. It can detect when an S3 bucket or KMS key is accessible to external accounts or the public internet.
It generates findings that administrators can review and remediate. This is crucial for preventing data leaks and ensuring compliance with data protection regulations.
- Available for S3, KMS, Lambda, SQS, and more.
- Supports both AWS-managed and customer-managed policies.
- Can be automated using AWS Config rules.
According to AWS, Access Analyzer reduces misconfiguration risks by up to 70%.
Real-Time Threat Detection with Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior. It analyzes CloudTrail logs, VPC flow logs, and DNS logs to identify threats like compromised credentials, reconnaissance, or data exfiltration.
GuardDuty can detect:
- Use of stolen access keys.
- Unusual API call patterns (e.g., mass data downloads).
- Communication with known malicious IPs.
When a threat is detected, GuardDuty generates a finding that can trigger automated responses via AWS Lambda or alert security teams through Amazon SNS.
Best Practices and Future Trends in Identity Management AWS
As cyber threats evolve and cloud adoption accelerates, Identity Management AWS must keep pace. This final section outlines proven best practices and emerging trends shaping the future of cloud identity.
Top 7 Best Practices for Identity Management AWS
1. Enable MFA for all users, especially the root account.
2. Use roles instead of long-term access keys for applications and services.
3. Regularly rotate credentials and remove unused users and policies.
4. Apply the principle of least privilege in all policy designs.
5. Monitor and audit access using CloudTrail and GuardDuty.
6. Use AWS Organizations and SCPs for multi-account governance.
7. Automate identity provisioning with SSO and SCIM.
These practices form the foundation of a secure and scalable identity strategy.
The Rise of Identity as a Service (IDaaS)
The future of Identity Management AWS is increasingly moving toward Identity as a Service (IDaaS) models. Services like AWS SSO, Amazon Cognito, and third-party platforms like Okta and Auth0 are making identity management more accessible, scalable, and intelligent.
IDaaS offers:
- Reduced operational overhead.
- Enhanced user experience with single sign-on.
- Advanced features like adaptive authentication and risk-based access control.
As AI and machine learning are integrated into identity systems, we can expect smarter anomaly detection and automated policy recommendations.
Zero Trust Architecture and Identity-First Security
The zero trust model—“never trust, always verify”—is becoming the gold standard for cloud security. In this model, Identity Management AWS is not just a component; it is the foundation.
Zero trust requires:
- Continuous authentication and authorization.
- Micro-segmentation of access.
- Real-time risk assessment based on user behavior and device health.
AWS is well-positioned to support zero trust through its comprehensive identity and monitoring tools. The future belongs to organizations that treat identity as their primary security boundary.
What is Identity Management AWS?
Identity Management AWS refers to the set of services and policies—primarily AWS IAM—that control access to AWS resources. It includes managing users, roles, groups, and permissions to ensure secure and compliant operations in the cloud.
How do I enable MFA in AWS?
To enable MFA, go to the IAM console, select a user, and choose ‘Assign MFA device’. You can use a virtual MFA app, U2F key, or hardware device. Once configured, require MFA in policies using the ‘aws:MultiFactorAuthPresent’ condition key.
What is the difference between IAM roles and IAM users?
IAM users have long-term credentials (like passwords and access keys) and represent individuals. IAM roles provide temporary credentials and are assumed by users, applications, or services when they need specific permissions, promoting security through short-lived access.
Can I use my corporate Active Directory with AWS?
Yes. AWS Directory Service allows integration with on-premises Active Directory via AD Connector or AWS Managed Microsoft AD, enabling users to log in to AWS using their corporate credentials.
What is AWS SSO and how does it work?
AWS Single Sign-On (SSO) enables users to access multiple AWS accounts and cloud applications using a single set of corporate credentials. It integrates with AWS Organizations and supports SAML-based federation and SCIM for automated user provisioning.
Identity Management AWS is not just a technical necessity—it is a strategic imperative. From securing individual users to enabling enterprise-wide governance, AWS provides a comprehensive, evolving platform for managing digital identities in the cloud. By embracing best practices, leveraging automation, and preparing for future trends like zero trust and IDaaS, organizations can build resilient, compliant, and agile cloud environments. The power to control access is the power to protect value—and in the AWS cloud, identity is that power.
Further Reading: